Sync Function Reference
About Sync Gateway Roles and their part in secure cloud-to-edge enterprise data synchronization.
Here we introduce the concept of Roles and the part they play in assuring secure access control within Sync Gateway.
Related Topics: Concepts | How-to | Sync Function | Use XATTRs for Access Grants
Concept
The sync function is crucial to the security of your application. It is in charge of data validation, access control and routing. The function executes every time a new revision/update is made to a document.
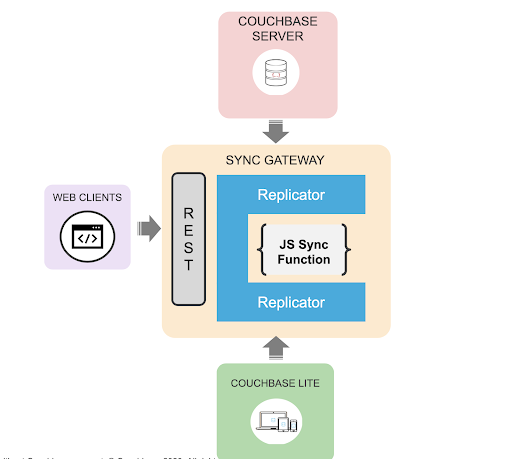
The sync function should be a focus of any security review of your application.
Use
The Sync Function exposes a number of helper functions to control access — see reference information in Sync Function API. For example, to grant a user access to a channel use the access() helper function in the Sync Function.
The access() function can also operate on roles.
If a user name string begins with role: then the remainder of the string is interpreted as a role name.
There’s no ambiguity here, because ":" is an illegal character in a user or role name.
Because anonymous requests are authenticated as the user "GUEST", you can make a channel and its documents public by calling access with a username of GUEST.
You will likely need to include a check for deleted documents and to treat these differently when validating. A deletion is just a revision with a "_deleted": true property; and usually nothing else.
Any validation checks will probably fail because of the missing properties, so build -in a check for doc._deleted == true.
Sync Function Prototype
-
Version 3.x
-
All Versions
function (doc, oldDoc, meta) { (1)
channel(doc.channels); (2)
}function (doc, oldDoc) {
channel(doc.channels); (1)
}| 1 | [This prototype shows the default Sync Function — see Arguments for more on the arguments.] |
Arguments
The sync function arguments are:
| Name | Description |
|---|---|
|
This object references the content of the document that is being saved. It matches the JSON saved by the Couchbase Lite application and replicated to Sync Gateway. The document’s |
|
If the document has been saved before, this object references the revision being replaced; otherwise it is null. Your implementation of the sync function can omit the |
|
From 3.0 the Sync Function includes support for a new This argument references the user defined XATTR that you can use to hold access grant data. The referenced object can include items such as channels or roles. So instead of embedding channel information directly within the document body, users can specify the user-defined XATTR associated with the document — see Use XATTRs for Access Grants. |
Configuration
If you don’t supply a sync function, Sync Gateway uses the default Sync Function.
-
Version 3.x
-
All Versions
Here we use the Database Configuration API to provision our Sync Function — see: Database Configuration
The example uses CURL to do this, but you may use a mechanism of your choice.
curl --location --request PUT 'http://localhost:4985/getting-started-db/_config' \
--header 'accept: application/json' \
--header 'Content-Type: application/json' \
--data-raw '{
"sync": ` /* sync function code */ ` (1)
}'
Users running version v3.0+ must run with disable-persistent-configuration=true
|
Here we embed our Sync Function in our Sync Gateway configuration file.
// ... may be preceded by additional configuration data as required by the user ...
"databases": {
"getting-started-db": {
"name": "getting-started-db",
"bucket": "getting-started-bucket",
"import_docs": true,
"num_index_replicas": 0,
"sync": `/* sync function code */` (1)
}
}| 1 | Insert the Sync Function code, for example from Example 3 here. Note the sync function is enclosed in backticks. |
Example
When you come to build your Sync Function you will need to decide the access control and document distribution requirements. For example:
-
The document types it will process
-
The users it will serve
-
Which users need to access which document types
-
What constraints are to be be placed on creating, updating and-or deleting documents
Our requirements for this example are:
| 1 | That all documents have the following properties: creator, writers, title channels |
| 2 | That we allow only create and-or delete access to users with the role editor |
| 3 | That we only allow changes, including deletions, to be made by users identified in the document’s writers property |
| 4 | That the creator is immutable |
| 5 | That we will assign the document to the channel(s) identified within the documents contents or metadata (v3.0+). |
-
Version 3.x
-
All Versions
You can use XATTR contents to drive access control.
// Note the new (3.0), optional, argument `meta`
function (doc, oldDoc, meta) {
if (doc._deleted) {
// Only editors with write access can delete documents:
requireRole("role:editor"); (2)
requireUser(oldDoc.writers); (3)
// Skip other validation because a deletion has no other properties:
return;
}
// Required properties:
if (!doc.title || !doc.creator ||
!doc.channels || !doc.writers) { (1)
throw({forbidden: "Missing required properties"});
} else if (doc.writers.length == 0) {
throw({forbidden: "No writers"});
}
if (oldDoc == null) {
// Only editors can create documents:
requireRole("role:editor"); (2)
// The 'creator' property must match the user creating the document:
requireUser(doc.creator)
} else {
// Only users in the existing doc's writers list can change a document:
requireUser(oldDoc.writers); (3)
// The "creator" property is immutable:
if (doc.creator != oldDoc.creator) {
throw({forbidden: "Can't change creator"}); (4)
}
}
// Finally, assign the document to the channels in the list:
channel(meta.xattrs.[xattrName]); (5)
}Here we will use the document content to drive the channels to be accessed — using doc.channels
function (doc, oldDoc) {
if (doc._deleted) {
// Only editors with write access can delete documents:
requireRole("role:editor"); (2)
requireUser(oldDoc.writers); (3)
// Skip other validation because a deletion has no other properties:
return;
}
// Required properties:
if (!doc.title || !doc.creator ||
!doc.channels || !doc.writers) { (1)
throw({forbidden: "Missing required properties"});
} else if (doc.writers.length == 0) {
throw({forbidden: "No writers"});
}
if (oldDoc == null) {
// Only editors can create documents:
requireRole("role:editor"); (2)
// The 'creator' property must match the user creating the document:
requireUser(doc.creator)
} else {
// Only users in the existing doc's writers list can change a document:
requireUser(oldDoc.writers); (3)
// The "creator" property is immutable:
if (doc.creator != oldDoc.creator) {
throw({forbidden: "Can't change creator"}); (4)
}
}
// Finally, assign the document to the channels in the list:
channel(doc.channels); (5)
}access()
- Function
-
access(username, channelname)
Arguments
| Argument | Description |
|---|---|
username |
Must be a string identifying a user, or an array of strings identifying multiple users; the function is applied to each user in the array. If the value resolves to null the function result is a no-op. |
|
Must be a string identifying a channel name, or an array of strings to specify multiple channel names (for example: If the value resolves to null the function result is a no-op. |
As a convenience, the resolved value of either argument may be null or undefined, in which case nothing happens.
|
Context
You can invoke this function multiple times from within your Sync Function.
Prefix the username argument value with role: to apply this function to a role rather than a user.
This grants access to the specified channel(s) for all users assigned that role.
|
The effects of all access calls by all active documents are effectively combined in a union, so if any document grants a user access to a channel, that user has access to the channel.
You can use the all channels wildcard ('*') to grant the user access to all documents in all channels.
Use
This example shows some valid ways to call access():
access ("jchris", "mtv"); (1)
access ("jchris", ["mtv", "mtv2", "vh1"]); (2)
access (["snej", "jchris", "role:admin"], "vh1"); (3)
access (["snej", "jchris"], ["mtv", "mtv2", "vh1"]); (4)
access (null, "hbo"); (5)
access ("snej", null);| 1 | Allow access of single channel to single user |
| 2 | Allow access of multiple channels to single user |
| 3 | Allow access of single channel to multiple users |
| 4 | Allow access of multiple channels to multiple users |
| 5 | The null arguments mean these are treated as no-ops |
If you invoke the access() function multiple times to grant the same user access to the same channel, you could see negative performance effects, such as large fetches or request timeouts.
|
channel()
Arguments
| Argument | Description |
|---|---|
|
Must be a string identifying a channel name, or an array of strings to specify multiple channel names (for example: If the value resolves to null the function result is a no-op. |
Context
The channel function can be called zero or more times from the sync function, for any document.
|
Channels don’t have to be predefined. A channel implicitly comes into existence when a document is routed to it. |
Routing changes have no effect until the document is actually saved in the database, so if the sync function first calls channel() or access(), but then rejects the update, the channel and access changes will not occur.
As a convenience, it is legal to call channel with a null or undefined argument; it simply does nothing.This allows you to do something like channel(doc.channels) without having to first check whether doc.channels exists.
|
expiry()
- Function
-
expiry(value)
Arguments
| Argument | Description |
|---|---|
|
The
|
1 Couchbase Server expiries are specified as Unix time, and if the desired TTL is below 30 days then it can also represent an interval in seconds from the current time (for example, a value of 5 will remove the document 5 seconds after it is written to Couchbase Server).
Context
Under the hood, the expiration time is set and managed on the Couchbase Server document (TTL is not supported for databases in walrus mode).
Impact
The impact on the resulting document when the expiry value is reached depends on the setting of shared-bucket-access:
- Enabled
-
The active revision of the document is tombstoned.
If there is another non-tombstoned revision for this document (i.e a conflict) it will become the active revision.
The tombstoned revision will be purged when the server’s metadata purge interval is reached.
- Disabled
-
The document will be purged from the database.
As with the existing explicit purge mechanism, this applies only to the local database; it has nothing to do with replication.
This expiration time is not propagated when the document is replicated.
The purge of the document does not cause it to be deleted on any other database.
Inspect a Document Expiry Value
You can retrieve a document’s expiration time, as it is returned in the response of GET +/\{db/{doc} use show_exp=true as the querystring.
curl -X GET "http://localhost:4985/ourdb/ourdoc?show_exp=true" -H "accept: application/json"requireAccess()
- Function
-
requireAccess(channels)
Purpose
Use the requireAccess() function to reject document updates that are not made by the a user with access to at least one of the given channels, as shown in Example 7
Arguments
| Argument | Description |
|---|---|
|
Must be a string identifying a channel name, or an array of strings to specify multiple channel names (for example: If the value resolves to null the function result is a no-op. |
Context
The function signals rejection by throwing an exception, so the rest of the sync function will not be run.
Note that requireAccess() will only recognize grants made explicitly using a channel name (not by a wildcard).
So, if a user was granted access using only the all channels wildcard] (*), then requireAccess('anychannelname')' will fail because the user wasn’t granted access to that channel (only to the * channel).
Use
requireAccess("events"); (1)
if (oldDoc) {
requireAccess(oldDoc.channels); (2)
}| 1 | Throw an exception unless the user has access to read the "events" channel: |
| 2 | Throw an exception unless the user can read one of the channels in the previous revision’s channels property: |
requireRole()
- Function
-
requireRole(rolename)
Purpose
Use the requireRole() function to reject document updates that are not made by user with the specified role or roles, as shown in Example 9.
Arguments
| Argument | Description |
|---|---|
|
Must be a string identifying a role, or an array of strings identifying multiple roles; the function is applied to each role in the array. If the value resolves to null the function result is a no-op. Note — Role names must always be prefixed with |
requireUser()
- Function
-
requireUser(username)
Purpose
Use the requireUser() function to reject document updates that are not made by the specified user or users.
Arguments
| Argument | Description |
|---|---|
username |
Must be a string identifying a user, or an array of strings identifying multiple users; the function is applied to each user in the array. If the value resolves to null the function result is a no-op. |
Context
The function signals rejection by throwing an exception, so the rest of the sync function will not be run.
When validating a document, you should treat all properties of the doc parameter as untrusted. That is because it is the object that you’re validating.
This may sound obvious, but it can be easy to make mistakes, like calling requireUser(doc.owners) instead of requireUser(oldDoc.owners).
When using one document property to validate another, look up that property in oldDoc, not doc!
role()
- Function
-
role(username, rolename)
Purpose
Use the role() function to add a role to a user.
This indirectly gives them access to any channels assigned to that role.
| Roles, like users, have to be explicitly created by an administrator. |
Arguments
| Argument | Description |
|---|---|
|
Must be a string identifying a role, or an array of strings identifying multiple roles; the function is applied to each role in the array. If the value resolves to null the function result is a no-op. Note — Role names must always be prefixed with |
username |
Must be a string identifying a user, or an array of strings identifying multiple users; the function is applied to each user in the array. If the value resolves to null the function result is a no-op. |
Context
This function affects the user’s ability to revise documents, if the access function requires role membership to validate certain types of changes.
Its use is similar to access.
Nonexistent roles don’t cause an error, but have no effect on the user’s access privileges.
| You can create roles retrospectively. As soon as a role is created, any pre-existing references to it take effect. |
Use
role ("jchris", "role:admin"); (1)
role ("jchris", ["role:portlandians", "role:portlandians-owners"]); (2)
role (["snej", "jchris", "traun"], "role:mobile"); (3)
role ("ed", null); (4)| 1 | The role admin is assigned to the user |
| 2 | Both the named roles are assigned to the user |
| 3 | The role mobile is assigned to all the named users |
| 4 | No op |
throw()
- Function
-
throw()
Context
You enforce the validity of document structure by checking the necessary constraints and throwing an exception if they’re not met.
In validating a document, you’ll often need to compare the new revision to the old one, to check for illegal changes in state.
For example, some properties may be immutable after the document is created, or may be changeable only by certain users, or may only be allowed to change in certain ways.
That’s why the current document contents are given to the sync function, as the oldDoc parameter.
We recommend that you not create invalid documents in the first place. As much as possible, your app logic and validation function should prevent invalid documents from being created locally. The server-side sync function validation should be seen as a fail-safe and a guard against malicious access.
Use
In this example the sync function disallows all writes to the database it is in.
function(doc) {
throw({forbidden: "read only!"}) (1)
}| 1 | The document update will be rejected with an HTTP 403 "Forbidden" error code, with the value of the forbidden: property being the HTTP status message.This is the preferred way to reject an update. |